Popular Phishing Techniques used by Hackers


What Is Hacking? Types of Hacking & More

Evolution of Phishing Attacks
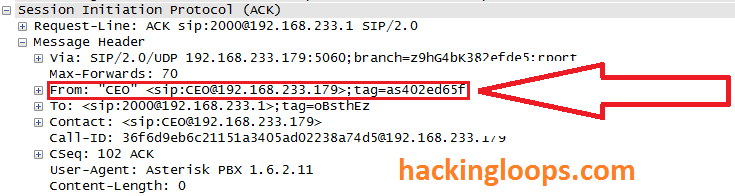
Penetration testing of VoIP : How Hackers Spoof Caller ID
Types of Phishing: A Comprehensive Guide

Spear Phishing vs. Phishing: Key Differences and Similarities - Spiceworks

DICT Region VI - 𝗙𝗬𝗜! ⚠️ 𝐅𝐨𝐫 𝐚𝐧𝐲 𝐜𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧𝐜𝐢𝐝𝐞𝐧𝐭 𝐜𝐨𝐧𝐜𝐞𝐫𝐧𝐬, 𝐲𝐨𝐮 𝐜𝐚𝐧 𝐫𝐞𝐚𝐜𝐡 𝐭𝐡𝐞 𝐂𝐲𝐛𝐞𝐫𝐜𝐫𝐢𝐦𝐞 𝐈𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐂𝐨𝐨𝐫𝐝𝐢𝐧𝐚𝐭𝐢𝐧𝐠 𝐂𝐞𝐧𝐭𝐞𝐫 𝐚𝐭 𝐭𝐡𝐞𝐬𝐞
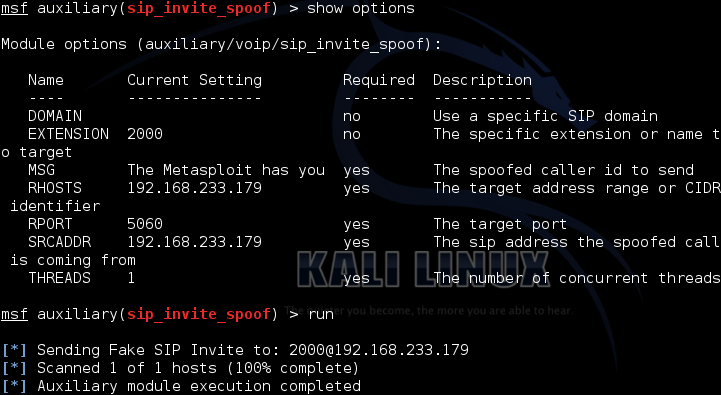
Penetration testing of VoIP : How Hackers Spoof Caller ID

Cyber crimes - web Jacking- The term refers to forceful taking of control of a web site by cracking - Studocu

Cyber Security - CS-503 (C) - Class Notes - 1563265709, PDF, Cybercrime

How Hackers Use Social Engineering Tactics in Phishing Scams
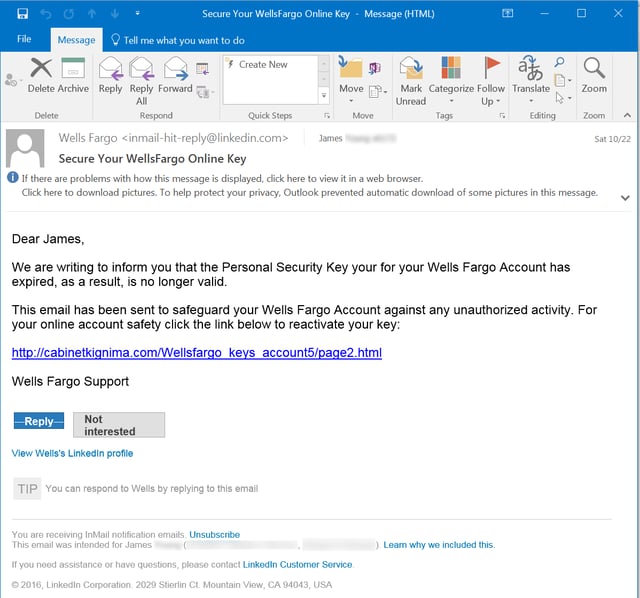
Phishing

Unit 5 - Cyber Security, PDF, Computer Virus